A lot of people ask me if they should implement DMARC or not and especially what it is really for (and if this will be useful for them)... The answer is below 🙂
DMARC, did you say DMARC?
What is it?
DMARC (Domain-based Message Authentication, Reporting and Conformance) is a standard (or technical specification) for monitoring problems related to email authentication and domain name abuse.
The objective of this standard is to fight more effectively against spam and phishing (see identity theft). It uses theSPF / DKIM authentication.
How does it work?
The operation is quite simple but it requires a technical mastery for its implementation. The following diagram aims to summarize and simplify the operation of DMARC:
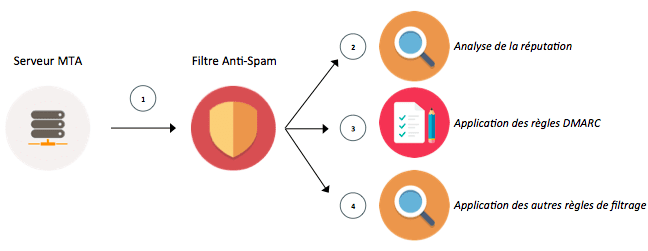
- An advertiser sends a mass campaign (or transactional message).
- The Anti-Spam filter analyzes the reputation of the advertiser (IP reputation, domain reputation, internal/external blacklist check). If it is bad, the message will be refused. If it is good, the message will be accepted and will go to point 3.
- The Anti-Spam filter will check the authentication systems and in case of failure will apply the security rule in accordance with the declaration made in the "p" tag. There are 3 possible settings:
- P=none; no rule will be applied, the message will be accepted.
- P=quarantine; the message will be tagged as spam and delivered as spam
- P=reject; the message will be rejected automatically.
DMARC rules only apply if the ISP/Webmails applies DMARC in its security policy. The interpretation of "quarantine" and "reject" may vary from one to another.
- If the message passes DMARC rules, it will be confronted with the latest filtering rules (content analysisgreen list, etc.)
How to implement it?
Prerequisites
For DMARC to be effective, you will need to set up the SPF and DKIM authentication systems and of course you will need to be the owner of the domain (it is preferable to implement DMARC on the main domain, which will also protect the sub-domains).
- Small reminder of SPF: Sender Policy Framework allows to declare in the TXT record of the domain (or subdomain) the IPs authorized to send e-mails.
- A quick reminder of DKIM: DomainKey Identified Mail allows you to sign a message using a cryptographic signature (public key - private key) and to ensure that it is not intercepted/modified during delivery.
So before you start implementing DMARC, make sure that SPF and DKIM are correctly implemented.
Feel free to use the following tools to verify this:
The implementation
The implementation remains simple, you just have to set the tag in the TXT record of the domain.
Need help?
Reading content isn't everything. The best way is to talk to us.
The tag is composed of "mandatory" elements:
- v : defines the protocol version
- p : defines the applicable security rule (values " none ", " quarantine ", " reject ")
But it can be composed of "optional" elements:
- pct: defines the percentage that will be filtered
- rua : defines the email address that will receive the DMARC report
- sp : defines the rule applicable to the sub-domains of the domain
- aspf : defines the alignment for SPF (values " s " for strict, " r " for relaxed)
- adkim : defines the alignment for DKIM (values " s " for strict, " r " for relaxed)
Points of vigilance
- Before installing DMARC on a domain (or sub-domain), be sure that all old settings (SPF/DKIM/DMARC) are removed, to avoid duplicates or rejections due to a "strict" setting or an oversight in the SPF declaration.
- Carry out an optimal DMARC setup in 10 weeks to make sure everything is ok before applying a maximum security level.
- 1era week : set to " none ".
- 2ème week: set to "quarantine" at 5%
- 3ème week: set to "quarantine" at 15%
- 4ème week: set to "quarantine" at 25%
- 5ème week: set to "quarantine" at 50%
- 6ème week: set to "quarantine" at 100%
- 7ème week: set to "reject" at 5%
- 8ème week: set to "reject" at 15%
- 9ème week: set to "reject" at 25%
- 10ème week: set to "reject" at 50%
- 11ème week: set to "reject" at 100%
- Apply DMARC on the main domain to protect the whole domain (and its subdomains). Do not forget to include in SPF, all IPs authorized to route e-mails with the domain (cf. IP of the professional router if you use one).
Conclusion
Now you have no excuse for not protecting your domain names. And this might even give you some positive points for your reputation 😉
Note that La Poste (since June 2017) now checks DMARC and applies the security rules (first in France).
Sources:
- https://support.google.com/a/answer/2466563?hl=fr
- https://fr.wikipedia.org/wiki/DMARC
- https://dmarc.org/
Badsender accompanies you in your DMARC deployment
Deploying DMARC is not to be done "lightly". It is more than just adding a new DNS record. Badsender accompanies its customers in securing their email flows via DMARC :
- Implementation of a solution of DMARC monitoring configuration of domain names, creation of filters and dashboards in the monitoring tool, creation of automated alerts, etc.
- Email flow audit : authentication verification of the different flows, validation of the domain name alignment, detection of illegitimate flows, ...
- Compliance of the different email sources : teams' competence increase, validation of modifications made, ...
- Progressive transition to a policy=reject Once an acceptable level of compliance is reached, gradual transition to a rejection policy.
- Configuration of BIMI
The philosophy of Badsender is to bring you the tools, but especially the skills so that your teams can become autonomous on the subject of DMARC. After an active phase of DMARC deployment, we remain available if needed as dedicated support.