This article is primarily for those who want to know what is behind these four letters: D K I M
If SPF registration remains little known, DKIM is, as for him, generally even less known. Just like SPF, we will try to explain in a few lines what DKIM is, what it is used for, how it works, how it is set up and how to check that it is well set up on a domain!
Definition of DKIM
DKIM - or DomainKeys Identified Mail - is an e-mail authentication standard using a cryptographic signature system that guarantees the integrity of the message from the moment it is sent until it is received by the recipient. A DKIM key is composed of a private key (which will be in your routing tool) and a public key (which will be found in the TXT record of your domain). These 2 keys will be linked for life by a selector! Without it, unfortunately, it will be impossible to know if your public key and private key match and therefore by definition if your e-mail is the one that left your servers...
If you want to know more about the history of DKIM, please visit the official website.
Why implement DKIM on all your domains?
Just like SPF, the primary objective of DKIM is to protect the sender of an e-mail from the risks related to spam and identity theft. And yes, as soon as your emails leave your sending servers, it becomes vulnerable (and more than one person will want to hurt him) !
But setting it up goes far beyond fighting spam and phishing. By deploying DKIM, you show the anti-spam filters that you are using the recommended technologies for your emailing. Be careful though, this will not make you a good advertiser but at least you will prove that you are not a pure spammer!
Just as I had mentioned in my article on SPFDon't think that you are safe from a spam or phishing attack because unfortunately for you, spam and phishing spare no one! (Even if you are a startup, a freelancer, a small business, etc.)
To conclude, the more you neglect the protection of your domains, the more likely it is that someone with bad intentions will try to use them for less than glorious purposes.
How does DKIM work in practice?
Its operation remains rather simple. When an e-mail is sent, it will contain a signature (the private key set up on your sending server is then used to encrypt the signature). Upon receipt, the remote server will query your domain's DNS zone to verify that the signature contained in your email, the public key set on your domain and the selector match.
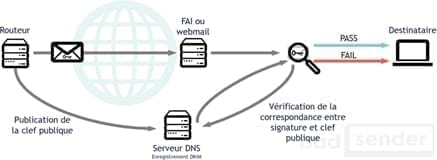
- If the public key, the email signature and the selector all match, it means that the message has not been tampered with while being sent and therefore comes from the sender.
- If the public key, the email signature and the selector do not match, it means that the message has been altered while being sent and therefore does not come from the sender it claims to be but from a third party trying to impersonate him.
Note Unlike SPF where you can only add one SPF record per domain, with DKIM you can have several public keys registered on your domain (for example, you use 2 routing tools, you can set up 1 key per routing tool, i.e. 2 keys).
Go go go... Let's go to the settings!
You have two options to create your DKIM key: either use an online tool or use the key from your business router!
Generate a DKIM key
With an online application: DKIMCore
DKIMCore is an online tool that will allow you to create a DKIM key. You will just have to enter your domain and the tool will generate your private key (to be added to your sending server), your public key and your selector (to be added to your domain).

With your professional router
This is the easiest way! Since you are using a professional routing tool, your ESP (see Email Service Provider) will provide you with your DKIM key by asking you directly to implement the public key (including the selector) on your domain and that's it
Note 1: You also have the possibility via your computer and the Putty Key Generator software (I used this method when I was young!) via WinSCP to create your DKIM key. If you are interested in this method, I refer you to this complete article of KDJ Webdesign.
Note 2: Google has been using 2048-bit encrypted keys for several years now, but most of the time we recommend that you at least have a 1024-bit encrypted key (or more). Personally (and that's just me)I'll opt for Google's format
Implement public & private key on your domain
As I told you several times, the public key is placed on the domain and more precisely in your TXT zone. The setting of the 2 keys will depend on the host you use and the router you use.
Public key configuration
Whether you create a DKIM key via an application or if your professional router provides it, the public key will be set up at your domain name host (it will be necessary to refer generally to the documentation provided by the host).
Configuration of the private key
As for the private key, if you are using a professional SaaS router like Actito, Sendinblue or even Mailjet, you will only need to add their public key to authenticate your domain. In some cases (I'm thinking of my Neolane years - Adobe Campaign now), you will need to add your private key (if you generated it) directly in the configuration of your instance (you will have to go through your technical documentation to find the right place).
Note the private key is... how to say... private (as its name indicates) and therefore must not be communicated to anyone!
And at Badsender, what does it look like?
Here is what we have declared in our domain Badsender.com and of course, I will only show you our public key
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDBMZ33Nv8+dde7Ovkp
PdxtT1DXnq0/idJhaKN6Bn4DxknuWwjQpxNmw3arr9/KE5knDt8nqBWsN6ZeebZCQ98u7RFrJO
7CiIL4iir1dFziQ1qT1SFXHN6zXPrzQAErPsoCxQsv7fUiPTB1nDFuAO6lRCMZNvOCP4pVORZ4
2u2KxQIDAQAB;It contains various information such as the DKIM version (v=), the mechanisms used to decode the DKIM signature (k=), the encoded public key (p=).
And the signature contained in an e-mail :
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=badsender.com; s=selector2; h=From:Date:Subject:Message-ID:Content-Type:MIME-Version:X-MS-Exchange-SenderADCheck; bh=atrqrzoOOt6QQ2ftP5NNkk7E3EJsyCAlwrSXXzbom5w=; b=HbGGbRIZh81OdUbGnkwW6pyZInXckMC6keL+VRUQrPTtfVm9Hbj4hBFHdtaxFuIjwFgB1Ra/jJ/w9pn9dr/KAey9oBNJV2wiOJ3VGAenvKRKta+7i18HVKQXmUITbzEUb4i/30OITDSPV1ib6nfnMHnYHkGaCGJ08P/4LHIkLP4=Here too, you will find a lot of information such as the DKIM version (v=), the signature algorithm (a=), the signed domain (d=), the selector (s=), the real signatures of the contents (b=), the hash of the body (bh=), ...
How to check if DKIM is correctly set up?
Personally, I only use one tool to check if DKIM is valid on a domain, it is DKIMCore. You can also use the Mxtoolbox or DMARCAnalyser.
To do this, you will need your domain name as well as the associated selector because without it, it is impossible to check your DKIM signature. If you don't know it, don't panic, just send an e-mail and check its SMTP header.
In the SMTP header of an email from Badsender (at Gmail)In green we find the selector used for the DKIM signature.
dkim=pass header.i=@badsender.com header.s=selector2 header.b=S0W1FpEi;Once you have the selector in your possession, simply enter them in the corresponding fields and the result is displayed.
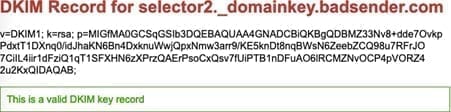
For those who like consoles more than graphic tools, you also have the possibility to check in command line via "Terminal" on MacOs (or MS-Dos if you are under Windows) your DKIM signature:
dig yourselector._domainkey.yourdomain TXTdig selector2._domainkey.badsender.com TXTWe check DKIM on the TXT record of the domain :
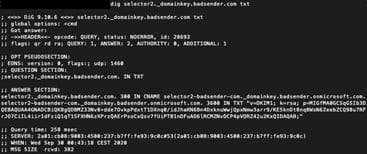
How to monitor DKIM?
Unfortunately, just like SPF, you will not be able to monitor DKIM directly (even via external tools) and therefore you will have no chance to find out if someone has tried to spoof your domain name.
However, just like SPF (again)there is an indirect way... DMARC ! Thanks to the reports sent by ISPs/Webmails checking DMARC, you can find out if someone has tried to spoof or use your domain name or if you have a faulty DKIM key.
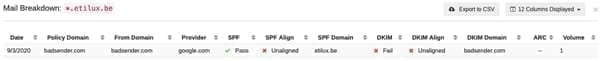
In the example above, we can see that the domain "*.etilux.be" has sent an e-mail with the domain "badsender.com", DKIM is declared "Fail". This raises the question of the legitimacy of this domain issuing e-mails from Badsender.com. Is it an identity theft or a simple e-mail transfer?
We conclude!?!
Once again, I hope this article will help you to better understand this complex authentication system and encourage you, if you haven't already done so, to set it up on all your domains (and sub-domains) because I am still surprised that in 2020, some advertisers have not yet set up DKIM on their domain (perhaps without knowing it)making him vulnerable...
If you have any questions, comments/comments, please do not hesitate to contact us You can also read our latest articles on e-mail authentication:
Leave a Reply