After a hectic summer with no downtime, I share our data with you today DMARC for the month of July & August 2021!
To summarize: Today, our security policy is at "quarantine", which means that any email with SPF & DKIM authentication failures will be delivered as junk mail to any organization (ISP, Webmails, companies, ...) able to interpret and apply the DMARC security rule.
Ultimately, we have two goals for 2021:
- Change our security policy from "quarantine" to "reject": we would then ask all ISPs/Webmails/Filters (interpreting DMARC) to reject emails with bad SPF & DKIM authentication.
- Legitimize all our email flows (and yes, we use several distinct tools for each type of sending - understand, we don't have all our eggs in the same basket :p).
Apply a "strict" SPF & DKIM alignment instead of a "relaxed" one: We're plugging EVERYTHING into Badsender.com!
This 3rd point is too complicated to set up (cf. point n°2), we will remain in "relaxed" since all our legitimate flows will be branded with a sub-domain of Badsender.com. And if one day things change... We will study a passage towards a strict alignment!
We are aware that it will take time and energy but it is not impossible! And if it allows us to reduce the risks of using our domain name, it's worth it.
Let's get to the heart of the matter... Enjoy your reading 🙂
July-August 2021 compliance rate
To be DMARC compliant, the email must return a properly authenticated and properly aligned (soft or hard) SPF or DKIM record.
Here are our results during the summer of 2021 (I voluntarily keep the history since the first DMARC monitoring was published to compare the evolution of the data):
| Badsender.com | Volumes | Compliant | Non-Compliant | Not Authenticated |
| August 2021 | 1 711 | 99,8% | 0,1% | 0,1% |
| July 2021 | 2 124 | 82,6% | 5,6% | 11,8% |
| June 2021 | 4 717 | 99,6% | 0,2% | 0,2% |
| May 2021 | 3 900 | 99,7% | 0,1% | 0,2% |
| April 2021 | 4 214 | 99,4% | 0,1% | 0,5% |
| March 2021 | 3 549 | 99,1% | 0,9% | 0,0% |
| February 2021 | 5 221 | 99,8% | 0,2% | 0,0% |
| January 2021 | 4 843 | 98,0% | 1,9% | 0,1% |
You can see that in July, our compliance rate was below 90%, due to a small spam wave. On the other hand, we found a "normal" rate (almost 100%) in August! Spammers never take a vacation 🙂
Authentication & SPF & DKIM alignment
For an email to be properly authenticated with SPF, the IP used must be declared in the SPF record of the email envelope domain (understand here the MailFrom/Return-path domain - visible in the SMTP header of an email).
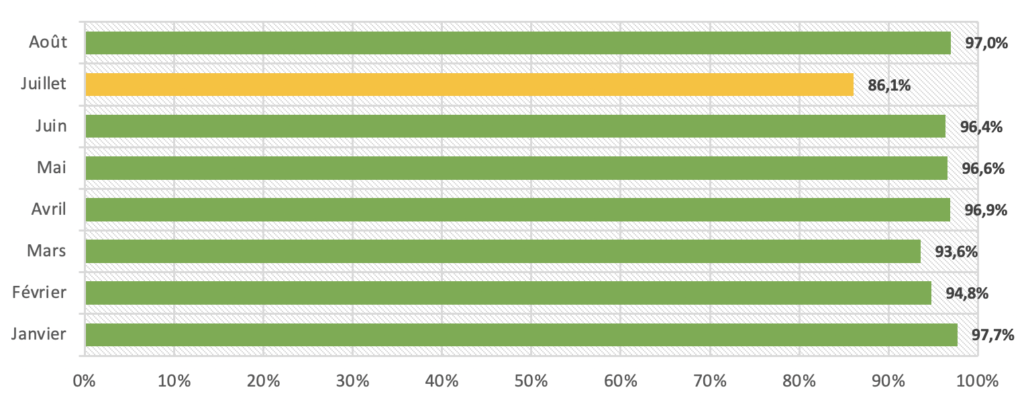
You'll notice that July was a hectic month... This is the first time our SPF authentication rate has fallen below 90%! And it's not our fault this time 🙂
And for an e-mail to be correctly aligned with SPF, the domain of the e-mail envelope (here the MailFrom/Return-path) must be identical or from a sub-domain of the FROM domain (cf. domain of the sending address).
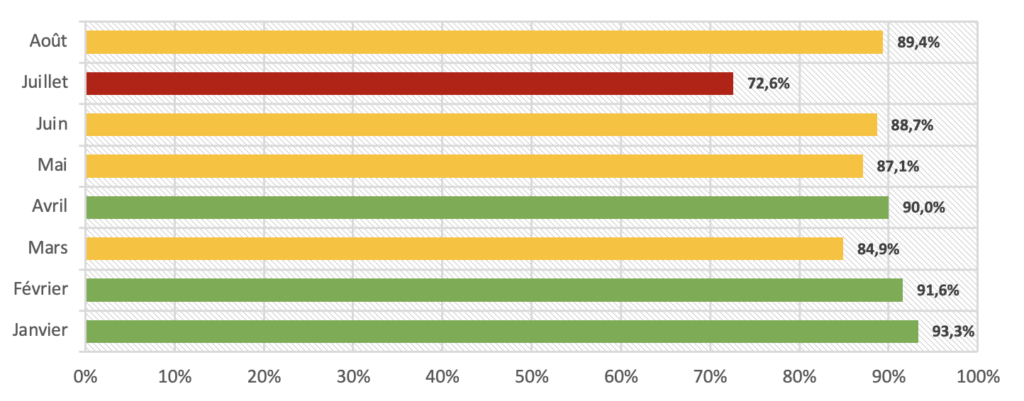
Some flows show an alignment problem but do not deserve any intervention from us. On the other hand, some flows still need to be optimized on our side so that SPF is fully aligned with DMARC.
For an email to be properly authenticated with DKIM, the email will need to have a valid DKIM signature (regardless of the domain used in the "d=" statement).
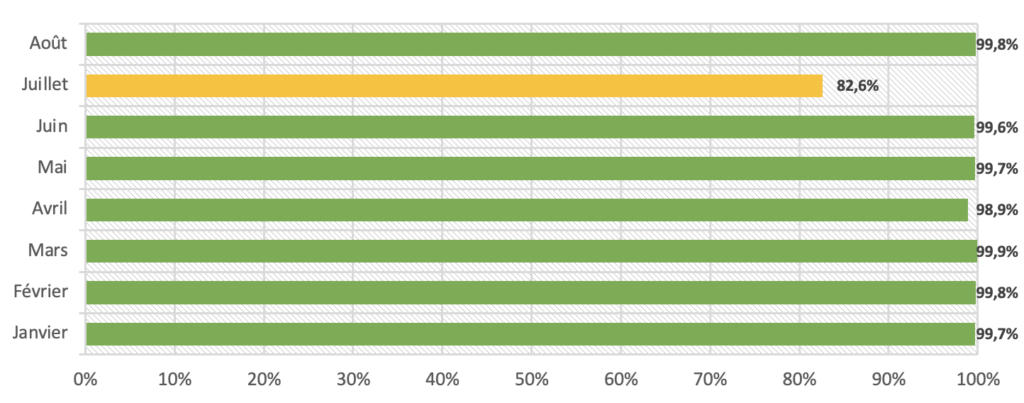
With the spam wave in July, our DKIM authentication rate was down. We found an almost perfect rate in August!
Need help?
Reading content isn't everything. The best way is to talk to us.
As far as DKIM alignment is concerned, for an e-mail to be correctly aligned, the domain declared in the DKIM signature (contained in the "d=") must be identical to or come from the sub-domain of the FROM domain (cf. domain of the sending address).
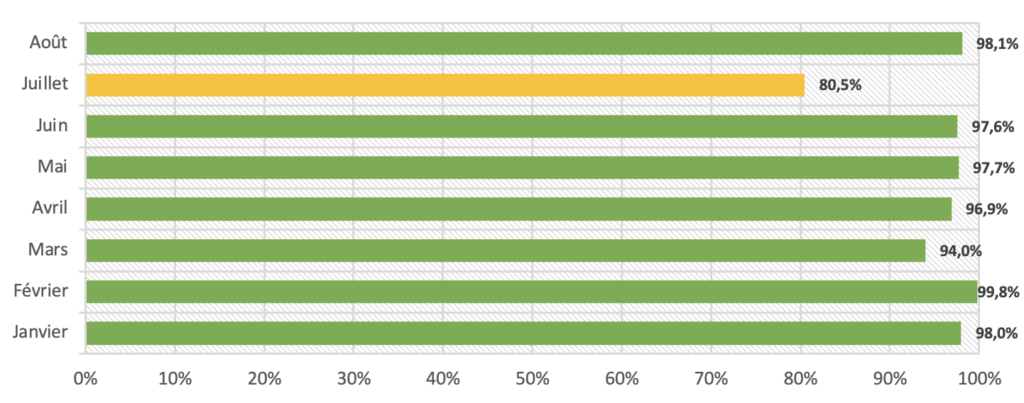
Like SPF alignment, some flows show authentication problems but do not deserve any intervention from us. On the other hand, some flows still need to be optimized on our side so that DKIM is also fully aligned with DMARC.
The last DKIM-related rate is the rate of unsigned e-mails (and yes, there are still some). These are emails that have no DKIM signature.
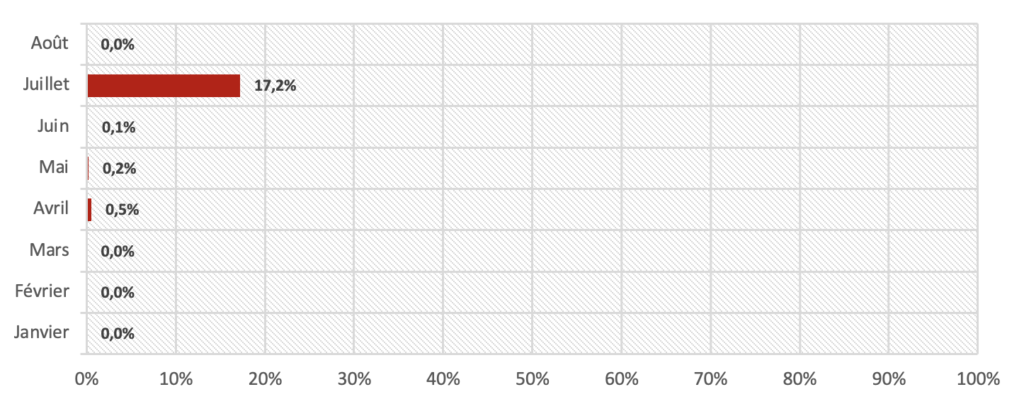
You will notice that in July our rate of unsigned emails has exploded... This is exclusively due to this famous spam wave!
Distribution of non-compliant & non-authenticated emails
Here is the list of "Sender rDNS" (understand here the domain name that is associated with an IP) reported as "non-compliant" on June 2021:
| Organization | Sender rDNS | Category | Volumes | Percentage | Source | Action |
| USA.net | *.mx.net | Webmail | 114 | 93.4% | Unknown | No action |
| Microsoft | *.outlook.com | Webmail | 2 | 1.7% | Unknown | No action |
| *.google.com | Webmail | 2 | 1.7% | Unknown | No action | |
| Sharpspring | *.marketingautomation.services | ESP | 1 | 0.8% | Known | Make it compliant |
| Verizon Media | *.yahoo.com | Webmail | 1 | 0.8% | Unknown | No action |
| CCM Benchmark | *.benchmark.fr | ESP | 1 | 0.8% | Unknown | No action |
| CCM Benchmark | *.ccmbg.com | ESP | 1 | 0.8% | Unknown | No action |
We have had a lot of non-compliant feedback from the rDNS sender "mx.net". Only Sharpspring's flow should be compliant (so will have to study and correct it).
And the list of "Sender rDNS" returned as "unauthenticated":
| Organization | Sender rDNS | Category | Volumes | Percentage | Source | Action |
| USA.net | *.mx.net | Webmail | 247 | 98.4% | Unknown | No action |
| Microsoft | *.outlook.com | Webmail | 2 | 0.8% | Unknown | No action |
| Unknown | Unknown | – | 2 | 0.8% | Unknown | No action |
The same goes for the "non-authenticated" flows... We have had a lot of feedback from the rDNS sender "mx.net". However, none of the flows need to be studied and corrected.
SPF & DKIM error trends
We have the possibility to know on each "Sender rDNS" what are the problems we have encountered and that will be corrected.
Below are the reported trends on SPF & DKIM errors for the month of June 2021:
Trend of the most frequent SPF errors
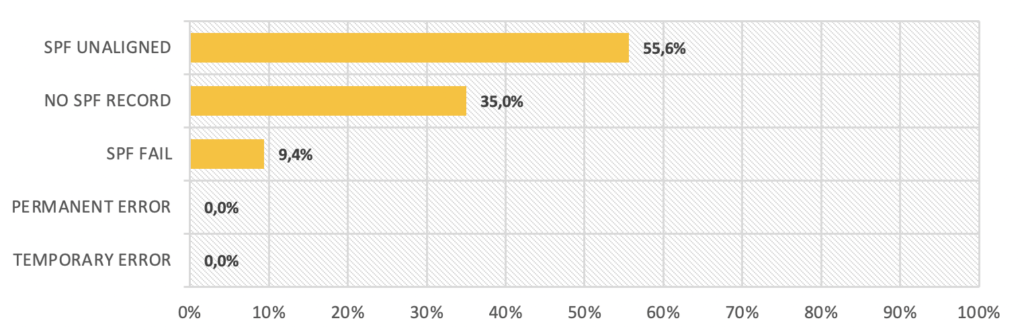
During the summer, 417 emails report an SPF alignment issue, 71 emails report SPF failure and 263 emails report an SPF authentication issue.
Trend of the most frequent DKIM errors
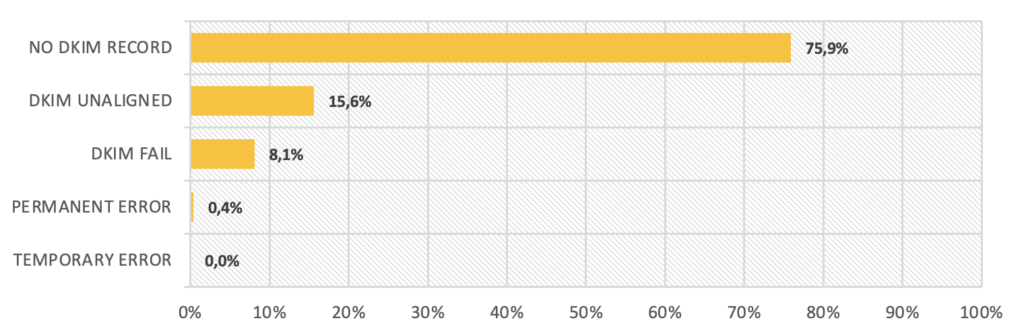
On the DKIM error side, 365 emails report a DKIM authentication issue, 75 emails report a DKIM alignment issue, 39 emails report DKIM failure and 2 emails report a permanent error.
Our roadmap for this September!
For the beginning of the school year, the objectives have not really changed compared to this summer:
- Finish our infrastructure migration.
- Correct the flows to be DMARC compliant.
- Upgrade our DMARC security policy to "quarantine" asap.
Conclusion
After a summer not really of any rest, we will be able to take again our conformity DMARC and seriously look at the flows that need to be fixed. Although before that, we already have to finalize our infrastructure migration (which is taking longer than expected).
Our other content related to DMARC (from near or far) :
- DMARC monitoring in June 2021
- DMARC monitoring in May 2021
- DMARC monitoring from April 2021
- DMARC monitoring from March 2021
- DMARC monitoring in February 2021
- DMARC monitoring from January 2021
- DMARC monitoring in December 2020
- DMARC Monitoring October vs. November 2020
- Tech 2021 #02 | What if you deploy DMARC in 2021 on your domain name?
- Our White Paper on DMARC deployment
- All about SPF in 3 articles:
- All about DKIM (1 article only):
- Almost everything you need to know about ARC (1 article so far):